Folder Options Recovery From Virus Attack
Some Current Indonesian Windows Viruses that were reported had widely spread out around the world had unique characteristics of attacking techniques. One of the old popular techniques was Changing (I like to call it “making a Mess”) Windows Folder Options by modifying Windows Registry.
Some Indonesian virus programmers preferred to play “hide and seek” only by hiding files in the computer target without making a dangerous destructive action of the computer system. Commonly, the attackers tried to hide the files by changing their file attributes into “hidden” and “system”, so that the files status is not just hidden, yet super-hidden as simply protected Windows system files.
The Victims cried that they had lost their such files. Some of them had realized that their files had been super-hidden, but they could not get their hidden files back since they could not change the Folder Options settings to the normal previous state after the virus programmer had ‘frozen’ the Folder Options Settings. And the rest of them did not realize that their files had just been invisible and, frequently, replaced by fake files (files that contain malicious scripts — the virus itself). Mostly, in the case of the frozen Folder Options Settings, the virus had made registry modifications at “Checked Value” and “Unchecked Value” Check Box Options.
This article tells about How To:
1. Unfreeze The Frozen Folder Options
2. Recover Folder Options Settings that had been changed by Virus
3. Show The Files that had been hidden by Virus
1. Unfreeze The Frozen Folder Options
There are two ways to Unfreeze The Frozen Folder Options. First, Kill The Resident Virus with trusted AntiVirus, and second, Recover Folder Options by re-modifying the registry keys that had been changed by attacking Virus to their normal previous state.
2. Recover Folder Options Settings that had been changed by Virus
2.1. Download Program : Folder Options Recovery for Windows v1.0.0
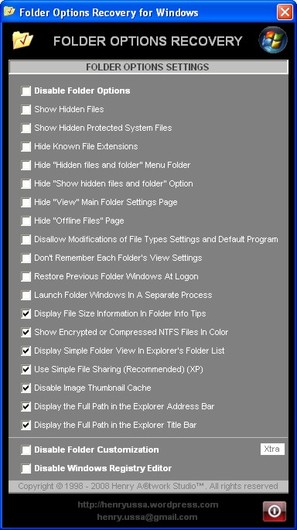
 NOTE : – Some Anti-Virus Programs had categorized this program as a computer threat (Trojan); that was just FALSE ALARM. I guarantee that this program does not contain any stupid malware and won’t harm Your computer. – FILE HAD BEEN RE-UPLOADED AND DOWNLOAD URL HAD BEEN RENEWED
NOTE : – Some Anti-Virus Programs had categorized this program as a computer threat (Trojan); that was just FALSE ALARM. I guarantee that this program does not contain any stupid malware and won’t harm Your computer. – FILE HAD BEEN RE-UPLOADED AND DOWNLOAD URL HAD BEEN RENEWED
– Category : Computer\Windows\Recovery Tools
– Program name : Folder Options Recovery for Windows
– Program Type : Portable Application
– Version : 1.0.0.0
– Supported OS : Microsoft Windows 98/Me/XP/Vista
– License : Freeware
– Developer : Henry U.S.S.A – Henry Artworks Studio
– File Name : Folder-Options-Recovery.exe
– File Size : 45.5 KB (46,592 bytes)
– Size On Disk : 48.0 KB (49,152 bytes)
– CRC-32 Checksum : A4B4949B
– MD5 : F1F60B1E84D8F1441AB59B92E347D22E
– SHA1 : 0E4D03F87A809D213C29300CADAFE2942577D80D
– Created : Monday, September 1st, 2008, 1:22:50 AM
2.2. Download Two Registry Entry Files below:
– a. Download Show_FolderOptions_and_ControlPanel.reg (download here)
– b. Download Folder_Options_Recovery_-_Show_All_Files.reg (download here)
—- and “Merge” it into Your Windows Registry Database, OR
2.3. Manual Recovery via Windows Registry by Creating Two Registry Entry Files:
– a. Open Windows Notepad or other Text Editors
– b. Copy these Registry Entry lines written below:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“NoFolderOptions”=dword:00000000
“NoControlPanel”=dword:00000000
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
“NoControlPanel”==dword:00000000
and save as Registry Entry File (.reg): “Show_FolderOptions_and_ControlPanel.reg“ -> this is useful for the condition if Folder Options had been hidden and Control Panel had been disabled by the Virus.
Yet, if Folder Options remains visible and Control Panel had not been disabled, then Copy and Paste into Your Notepad:
these Registry Entry lines written below:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder]
“Type”=”group”
“Text”=”@shell32.dll,-30498”
“Bitmap”=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,53,00,\
48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,34,00,00,\
00
“HelpID”=”shell.hlp#51140”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ClassicViewState]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30506”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”ClassicViewState”
“CheckedValue”=dword:00000000
“UncheckedValue”=dword:00000001
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51076”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ControlPanelInMyComputer]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\HideMyComputerIcons”
“Text”=”@shell32.dll,-30497”
“Type”=”checkbox”
“ValueName”=”{21EC2020-3AEA-1069-A2DD-08002B30309D}”
“CheckedValue”=dword:00000000
“UncheckedValue”=dword:00000001
“DefaultValue”=dword:00000001
“HKeyRoot”=dword:80000001
“HelpID”=”shell.hlp#51150”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\DesktopProcess]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30507”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”SeparateProcess”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51079”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\DesktopProcess\Policy]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\DesktopProcess\Policy\SeparateProcess]
@=””
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\DisableThumbCache]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30517”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”DisableThumbnailCache”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51155”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\FolderSizeTip]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30514”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”FolderContentsInfoTip”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\FriendlyTree]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30511”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”FriendlyTree”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“HelpID”=”shell.hlp#51149”
“DefaultValue”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Hidden]
“Text”=”@shell32.dll,-30499”
“Type”=”group”
“Bitmap”=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,53,00,\
48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,34,00,00,\
00
“HelpID”=”shell.hlp#51131”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Hidden\NOHIDDEN]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“Text”=”@shell32.dll,-30501”
“Type”=”radio”
“CheckedValue”=dword:00000002
“ValueName”=”Hidden”
“DefaultValue”=dword:00000002
“HKeyRoot”=dword:80000001
“HelpID”=”shell.hlp#51104”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Hidden\SHOWALL]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“Text”=”@shell32.dll,-30500”
“Type”=”radio”
“CheckedValue”=dword:00000001
“ValueName”=”Hidden”
“DefaultValue”=dword:00000002
“HKeyRoot”=dword:80000001
“HelpID”=”shell.hlp#51105”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\HideFileExt]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30503”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”HideFileExt”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000001
“HelpID”=”shell.hlp#51101”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\NetCrawler]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30509”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”NoNetCrawling”
“CheckedValue”=dword:00000000
“UncheckedValue”=dword:00000001
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51147”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\NetCrawler\Policy]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\NetCrawler\Policy\NoNetCrawling]
@=””
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\PersistBrowsers]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30513”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”PersistBrowsers”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“HelpID”=”shell.hlp#51152”
“DefaultValue”=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ShowCompColor]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30512”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”ShowCompColor”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000001
“HelpID”=”shell.hlp#51130”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ShowFullPath]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30504”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CabinetState”
“ValueName”=”FullPath”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51100”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ShowFullPathAddress]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30505”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CabinetState”
“ValueName”=”FullPathAddress”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000001
“HelpID”=”shell.hlp#51107”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\ShowInfoTip]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30502”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”ShowInfoTip”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“DefaultValue”=dword:00000001
“HelpID”=”shell.hlp#51102”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\SuperHidden]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30508”
“WarningIfNotDefault”=”@shell32.dll,-28964”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”ShowSuperHidden”
“CheckedValue”=dword:00000000
“UncheckedValue”=dword:00000001
“DefaultValue”=dword:00000000
“HelpID”=”shell.hlp#51103”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\SuperHidden\Policy]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\SuperHidden\Policy\DontShowSuperHidden]
@=””
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Thickets]
“Text”=”Managing pairs of Web pages and folders”
“Type”=”group”
“Bitmap”=”C:\\WINDOWS\\System32\\\\SHELL32.DLL,4”
“HelpID”=”TBD”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Thickets\AUTO]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer”
“Text”=”Show and manage the pair as a single file”
“Type”=”radio”
“CheckedValue”=dword:00000000
“ValueName”=”NoFileFolderConnection”
“DefaultValue”=dword:00000000
“HKeyRoot”=dword:80000001
“HelpID”=”TBD”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Thickets\NOHIDE]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer”
“Text”=”Show both parts but manage as a single file”
“Type”=”radio”
“CheckedValue”=dword:00000002
“ValueName”=”NoFileFolderConnection”
“DefaultValue”=dword:00000000
“HKeyRoot”=dword:80000001
“HelpID”=”TBD”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\Thickets\NONE]
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer”
“Text”=”Show both parts and manage them individually”
“Type”=”radio”
“CheckedValue”=dword:00000001
“ValueName”=”NoFileFolderConnection”
“DefaultValue”=dword:00000000
“HKeyRoot”=dword:80000001
“HelpID”=”TBD”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folder\WebViewBarricade]
“Type”=”checkbox”
“Text”=”@shell32.dll,-30510”
“HKeyRoot”=dword:80000001
“RegPath”=”Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced”
“ValueName”=”WebViewBarricade”
“CheckedValue”=dword:00000001
“UncheckedValue”=dword:00000000
“HelpID”=”shell.hlp#51148”
“DefaultValue”=dword:00000000
— 2.3. Save Text Lines above as a Registry Entry File (file format: .reg) : “Fix_Folder_Options.reg“
— 2.4. “Merge” it into Windows Registry Database:
3. Show The Files that had been hidden by Virus
After The Registry Entry Files had been merged successfully into Windows Registry Database, Folder Options will be ‘Your own’, and All Hidden Files (including Hidden System Files) will be shown with their unchanged file attributes (hidden and system attributes).
Then, finally You can simply manually change their file attributes back to their original attributes by a free recommended software named Attribute Changer that can be downloaded from here or directly from here.
NOTE:
The Resident Virus must be killed first with trusted AntiVirus (as the easiest way) before You can merge the Registry Entry File above into the Windows Registry Database to Recover Folder Options, or It won’t Work since the Virus will put the Folder Options Setting back to the wrong way…
Related and Supported Topic:
Memunculkan File Yang Disembunyikan Virus
Gracias
Filed under: Malware, Portable Application, Recovery, Security, Software, Virus, Windows, Windows Registry, Windows Vista, Windows XP | Tagged: Application | 21 Comments »
 ₪ NOTE : FILE HAD BEEN RE-UPLOADED and DOWNLOAD URL HAD BEEN RENEWED
₪ NOTE : FILE HAD BEEN RE-UPLOADED and DOWNLOAD URL HAD BEEN RENEWED























